How to Configure Tor to Work Through a Bridge Relay and Proxy in Windows
June 7, 2021
If you want to install Tor as a service on Windows, then you need the Expert Bundle. It can be downloaded from this page of the official website.
From the downloaded archive (in my case, the file is called tor-win32-0.4.5.8.zip), unpack the Tor folder to the root of the C drive.
Configuring Tor to Work Through a Bridge Relay
Theory: Some ISPs are blocking Tor. They can use various approaches, for example, block connections to all IPs of the Tor network, or by analyzing traffic and, if it is identified as belonging to the Tor network, block it.
Repeaters can be used to bypass this blockage. The bridge is one of the types of repeaters. Since not all bridge IP addresses are known, there is a chance to bypass Tor's blocking.
For this to work, you need obfs4 and a list of actual bridge IP addresses. The obfs4 source code can be obtained here:
It is written in the Go language. You can compile executables from source. I'll take the binaries from the Tor Browser. The required files are located in the \Browser\TorBrowser\Tor\PluggableTransports\ folder of your Tor Browser. Copy this folder to C:\Tor\.
You need to get a list of current IP addresses. To do this, follow the link: https://bridges.torproject.org/options
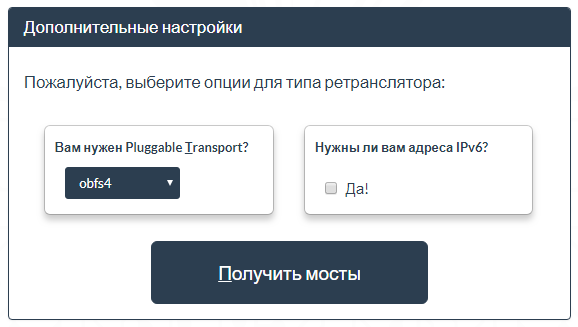
Select obfs4 and click the Get Bridges Button:
Enter captcha:
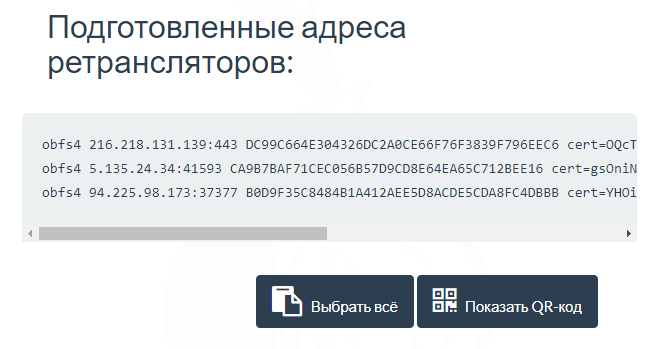
You will be given a list of three addresses. Copy one of these lines.
Another way to get bridges is to send an email to bridges@torproject.org. Please note that you must submit an email request using one of the listed services: Riseup, Gmail, or Yahoo.
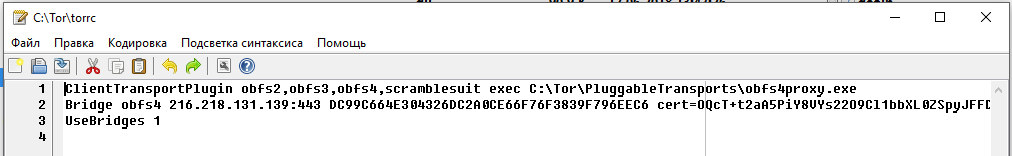
Now add to the C:\Tor\torrc file:
ClientTransportPlugin obfs2,obfs3,obfs4,scramblesuit exec C:\Tor\PluggableTransports\obfs4proxy.exe Bridge STRING UseBridges 1
Instead of STRING, insert one of those long lines that we got in the previous step:
It should look something like this:
ClientTransportPlugin obfs2,obfs3,obfs4,scramblesuit exec C:\Tor\PluggableTransports\obfs4proxy.exe Bridge obfs4 216.218.131.139:443 DC99C664E304326DC2A0CE66F76F3839F796EEC6 cert=OQcT+t2aA5PiY8VYs22O9Cl1bbXL0ZSpyJFFDikcZi3LVHOA4M/qrBhNF9MgxD8IbZLXdA iat-mode=0 UseBridges 1
Let's check:
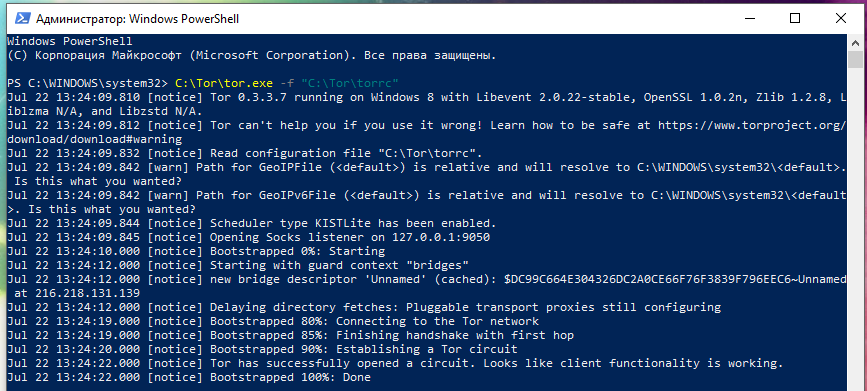
C:\Tor\tor.exe -f "C:\Tor\torrc"
Output example:
Jul 22 13:24:09.810 [notice] Tor 0.3.3.7 running on Windows 8 with Libevent 2.0.22-stable, OpenSSL 1.0.2n, Zlib 1.2.8, Liblzma N/A, and Libzstd N/A. Jul 22 13:24:09.812 [notice] Tor can't help you if you use it wrong! Learn how to be safe at https://www.torproject.org/download/download#warning Jul 22 13:24:09.832 [notice] Read configuration file "C:\Tor\torrc". Jul 22 13:24:09.842 [warn] Path for GeoIPFile (<default>) is relative and will resolve to C:\WINDOWS\system32\<default>. Is this what you wanted? Jul 22 13:24:09.842 [warn] Path for GeoIPv6File (<default>) is relative and will resolve to C:\WINDOWS\system32\<default>. Is this what you wanted? Jul 22 13:24:09.844 [notice] Scheduler type KISTLite has been enabled. Jul 22 13:24:09.845 [notice] Opening Socks listener on 127.0.0.1:9050 Jul 22 13:24:10.000 [notice] Bootstrapped 0%: Starting Jul 22 13:24:12.000 [notice] Starting with guard context "bridges" Jul 22 13:24:12.000 [notice] new bridge descriptor 'Unnamed' (cached): $DC99C664E304326DC2A0CE66F76F3839F796EEC6~Unnamed at 216.218.131.139 Jul 22 13:24:12.000 [notice] Delaying directory fetches: Pluggable transport proxies still configuring Jul 22 13:24:19.000 [notice] Bootstrapped 80%: Connecting to the Tor network Jul 22 13:24:19.000 [notice] Bootstrapped 85%: Finishing handshake with first hop Jul 22 13:24:20.000 [notice] Bootstrapped 90%: Establishing a Tor circuit Jul 22 13:24:22.000 [notice] Tor has successfully opened a circuit. Looks like client functionality is working. Jul 22 13:24:22.000 [notice] Bootstrapped 100%: Done
Notice the lines that talk about using the bridge:
Jul 22 13:24:12.000 [notice] Starting with guard context "bridges" Jul 22 13:24:12.000 [notice] new bridge descriptor 'Unnamed' (cached): $DC99C664E304326DC2A0CE66F76F3839F796EEC6~Unnamed at 216.218.131.139
And the line “Bootstrapped 100%: Done” indicates that the connection was successful.
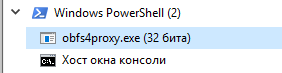
Note that obfs4proxy.exe is not unloaded after stopping Tor and even after closing the console:
You need to manually stop this process.
To find the PID:
netstat -aon | findstr ":9050"
To add to startup with settings:
C:\Tor\tor.exe --service install -options -f "C:\Tor\torrc"
Connecting to Tor via a proxy
You can connect to Tor through a proxy. The following types of proxies are supported:
- HTTP
- SOCKS5
- SOCKS4
If you are connecting via an HTTP proxy, then use the HTTPSProxy directive:
HTTPSProxy Proxy_IP:8888
Enter the IP address of the proxy server as Proxy_IP, and replace port 8888 with the desired one.
If you need to enter a username and password on the proxy, then do it like this:
HTTPSProxyAuthenticator USER:PASS
Replace USER with your username and replace PASS with your password.
When connecting via a SOCKS5 proxy, add to the configuration file:
Socks5Proxy Proxy_IP:8888
For Proxy_IP, enter the IP address of the SOCKS5 proxy server, and replace the 8888 port with the desired one.
If you need to log in, then the username and password can be entered like this (replace USER and PASS with actual data):
Socks5ProxyUsername USER Socks5ProxyPassword PASS
When connecting via a SOCKS4 proxy, add to the configuration file:
Socks4Proxy Proxy_IP:8888
For Proxy_IP, enter the IP address of the SOCKS5 proxy server, and replace the 8888 port with the desired one.
SOCKS4 does not support authentication.
Related articles:
- How to get web page content and cookies of .onion sites in Python (70.9%)
- Tor environment variables (59%)
- Script to connect and disconnect from OpenVPN depending on server availability (56.4%)
- How to download YouTube videos on Windows and Linux (GUI without third party services) (55.7%)
- How to prevent Tor users from viewing or commenting on a WordPress site (55.7%)
- Full-text search for documents in a folder (RANDOM - 51.3%)