How to check IP history for SSH sessions
October 15, 2021
How to list IP history of SSH sessions
If a Linux server has been hacked, it becomes necessary to collect information, for example, to get the time and IP addresses of the last SSH sessions. This can help not only identify the source of the danger, but also, for example, answer the question: was the SSH password brute-forced (or the certificate compromised) or an attacker exploited a software vulnerability.
Fortunately, Linux distributions keep logs of logins, both over the network and for users directly sitting in front of the computer.
IP address of the previous SSH connection
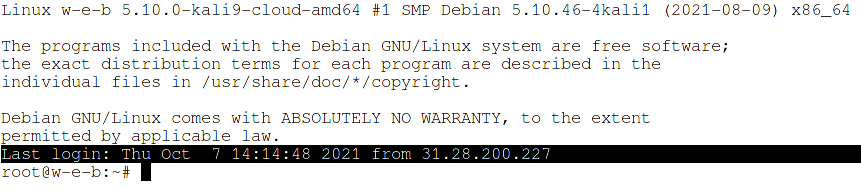
Each time you connect via SSH, a line is displayed with the IP from which the previous connection was made, the date and time of this connection is also displayed:
Last login: Thu Oct 7 14:14:48 2021 from 31.28.200.227
History of IP addresses of SSH connections
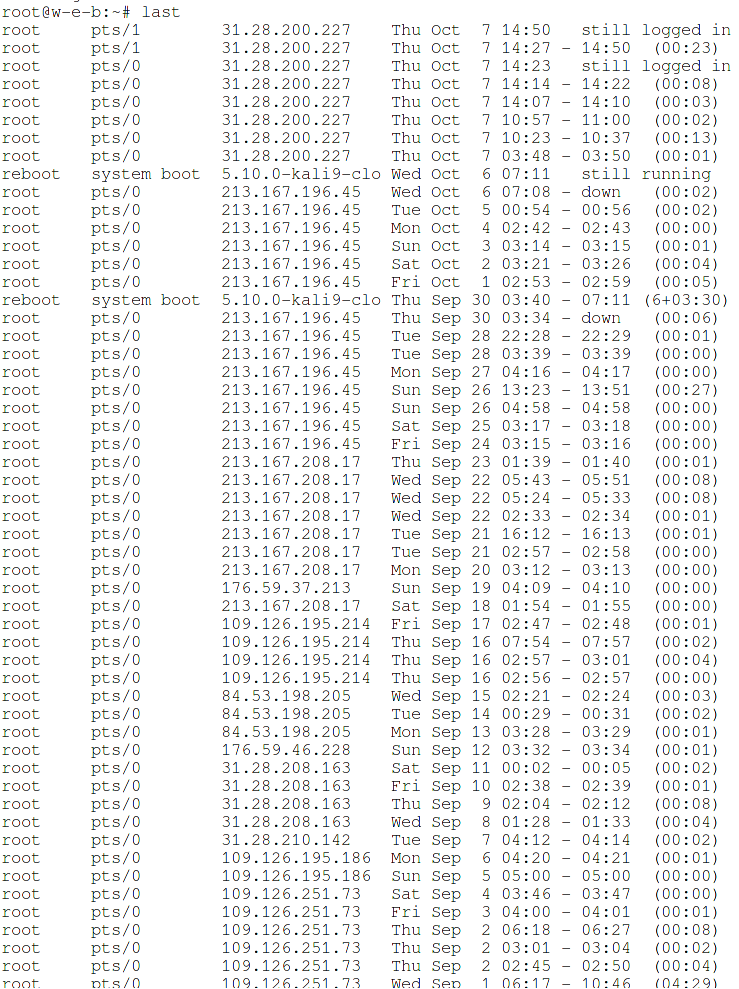
In addition to the last session, the system stores information about all successful logins for the last months. This information is contained in the utmp / wtmp file. In fact, the utmp file can be used by various programs (not just SSH) that want to preserve the user's login information.
Many distributions have a /var/log/wtmp file where programs write logins to the system. You can check the latest entries with the command:
last
All records containing IP addresses were made via SSH connection.
Entries without IP addresses are the logins of users directly in front of the computer.
Additionally you can check other log files: /var/log/secure (on RH based distributions) or /var/log/auth.log (on Debian based distributions). In these files, sshd usually keeps traces of connections made, even if they were not the result of successful logins (like utmp/wtmp does, which only keep track of successful logins).
Example:
Apr 3 16:21:01 xxxxxxvlp05 sshd[6266]: Connection closed by xxx.xxx.13.76 ... Apr 3 09:09:49 xxxxxxvlp05 sshd[26275]: Failed password for invalid user __super from xxx.xxx.13.76 port 45229 ssh2
The sshd service on IIRC Solaris (which is not necessarily the OpenSSH sshd service) stores this information in /var/adm/messages.
It should be remembered that if the attacker gained access with superuser rights, that is, the root account or another user with elevated privileges is compromised, then all entries in the files /var/log/wtmp or /var/adm/messages can be changed by the attacker. To protect against this, you must regularly upload logs to secure storage.
How to find out who is currently connected via SSH
To see the users logged in, use any of the following commands:
w who who -a
The following commands will also show active SSH sessions – each of them has a different set of output information, so you can choose the one that suits you best:
netstat -tnpa | grep 'ESTABLISHED.*sshd' ss -tap | grep 'ESTAB.*sshd' ps ax | grep sshd echo $SSH_CONNECTION
Related articles:
- GUI program to view and delete metadata in Linux (100%)
- How to change the VeraCrypt interface language in Linux (100%)
- How to make VirtualBox virtual machines destroy on computer restart (100%)
- Why computer can't connect to Wi-Fi Hotspot on Android phone for a long time (SOLVED) (100%)
- How to use Kali Linux to check web-sites (50%)
- Windows stopped booting in Virtual Machine after upgrading to VirtualBox 7 (SOLVED) (RANDOM - 50%)