Tag: Linux boot

How to migrate from X11 to Wayland?
Posted by Alex On February 12, 2024

How to change Display manager and login screen in Linux
Posted by Alex On February 11, 2024
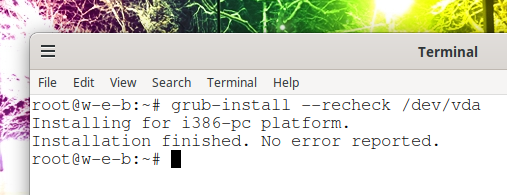
How to update the GRUB bootloader on Debian and derivative distributions (Kali Linux, Ubuntu, Linux Mint)
Posted by Alex On February 17, 2023

How to update the GRUB bootloader in Arch Linux and derivatives (Manjaro, BlackArch)
Posted by Alex On February 6, 2023

“Initramfs unpacking failed: invalid magic at start of compressed archive” error (SOLVED)
Posted by Alex On November 28, 2022

UEFI does not see installed Linux (SOLVED)
Posted by Alex On January 31, 2022

How to boot into VirtualBox from USB
Posted by Alex On November 11, 2021

How to repair an LVM disk using fsck
Posted by Alex On November 1, 2021

How to determine why Linux boots into Emergency mode
Posted by Alex On November 1, 2021

Error “Cannot open access to console, the root account is locked” (SOLVED)
Posted by Alex On October 26, 2021