Tag: Web Server

PHP Fatal error: Uncaught mysqli_sql_exception: No database selected (SOLVED)
Posted by Alex On September 6, 2023

“ERROR 1366 (22007): Incorrect string value” in MySQL/MariaDB (SOLVED)
Posted by Alex On August 26, 2023

PHP not displaying emoji from MySQL/MariaDB database (SOLVED)
Posted by Alex On August 25, 2023

How to get data from a web page using GET and POST methods in a Python script on Windows
Posted by Alex On May 21, 2023

How to get data from a web page using GET and POST methods in a Python script
Posted by Alex On May 21, 2023
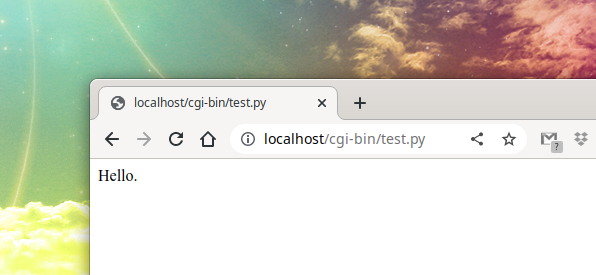
How to install Python as a CGI module in Apache on Linux
Posted by Alex On May 21, 2023
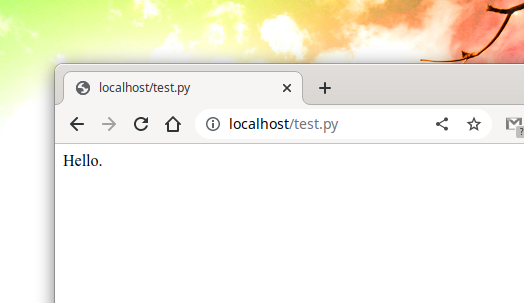
How to set up Python as a CGI module in Apache on Arch Linux (Manjaro, BlackArch)
Posted by Alex On May 21, 2023
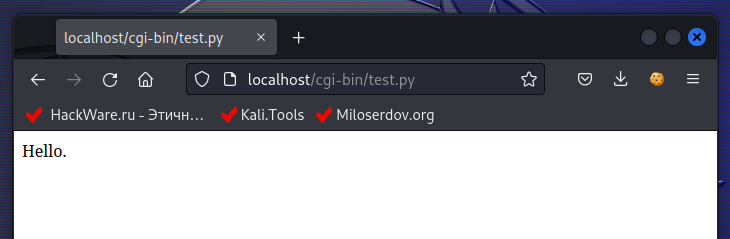
How to set up Python as a CGI module in Apache on Debian (Ubuntu, Linux Mint)
Posted by Alex On May 21, 2023

PHP Warning: PHP Startup: imap: Unable to initialize module (SOLVED). How to install the imap module for PHP on Arch Linux
Posted by Alex On April 8, 2023

Error “No such file or directory: AH02454: FCGI: attempt to connect to Unix domain socket /run/php/php8.1-fpm.sock (*:80) failed” (SOLVED)
Posted by Alex On January 29, 2023