Tag: file systems

How to find out when Linux was installed
Posted by Alex On April 21, 2023

How to increase the size of the partition and file system after increasing the physical size of the disk
Posted by Alex On March 23, 2023

How to check if a computer is using BIOS or UEFI; GRUB or systemd-boot bootloader; MBR or GPT partition table
Posted by Alex On June 17, 2022
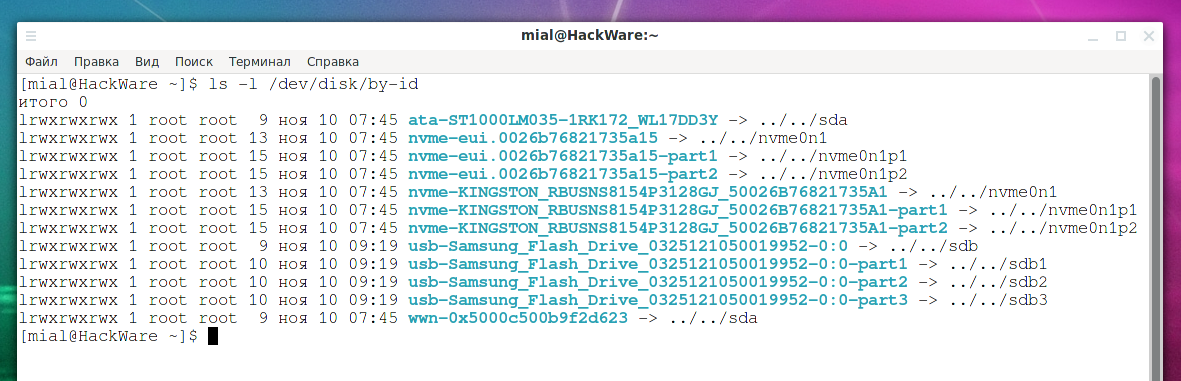
Persistent names for block devices
Posted by Alex On November 10, 2021

How to repair an LVM disk using fsck
Posted by Alex On November 1, 2021

How to determine why Linux boots into Emergency mode
Posted by Alex On November 1, 2021

Error “Cannot open access to console, the root account is locked” (SOLVED)
Posted by Alex On October 26, 2021

How to use lsof to view open files (on Linux everything is files)
Posted by Alex On October 18, 2021
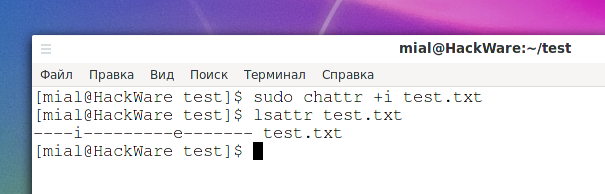
File attributes on Linux
Posted by Alex On October 14, 2021

An unplugged disk causes a delay in system boot
Posted by Alex On July 15, 2021