
How to install Kali Linux with encrypted user’s home folder (manual partitioning)
Posted by Alex On November 14, 2021
If the above automatic disk layout template with encryption of the home folder does not suit you, then you can configure disk layout manually, below is shown how to do it. With manual marking, remember that for a normal installation you need at least two partitions: EFI – 200 Megabytes is enough / (root of […]

How to install Kali Linux with encrypted user’s home folder (auto-partitioning)
Posted by Alex On November 14, 2021
The installer has a template for encrypting the user's home folder and it is perfect for novice users – the default settings are quite acceptable, the setup is very simple. The markup template has the following parameters: EFI partition – 500 MB /boot partition – 500 MB / (root) partition – 30 GB swap (swap […]

How to install Kali Linux with full disk encryption
Posted by Alex On November 14, 2021
This is the easiest option to set up and use – the entire drive will be encrypted. For encryption during the Kali Linux installation, as well as for use, you do not need to delve into how it works. Go to the page https://www.kali.org/get-kali/, in the Bare Metal section download the installation image. Using a […]

How to boot into VirtualBox from USB
Posted by Alex On November 11, 2021
In this post I will tell you how to connect a USB disk (or USB flash drive) to a virtual machine so that the guest system treats it like a regular hard disk. This trick will allow you not only to boot from the installation USB – which is rather pointless. If you connect a […]
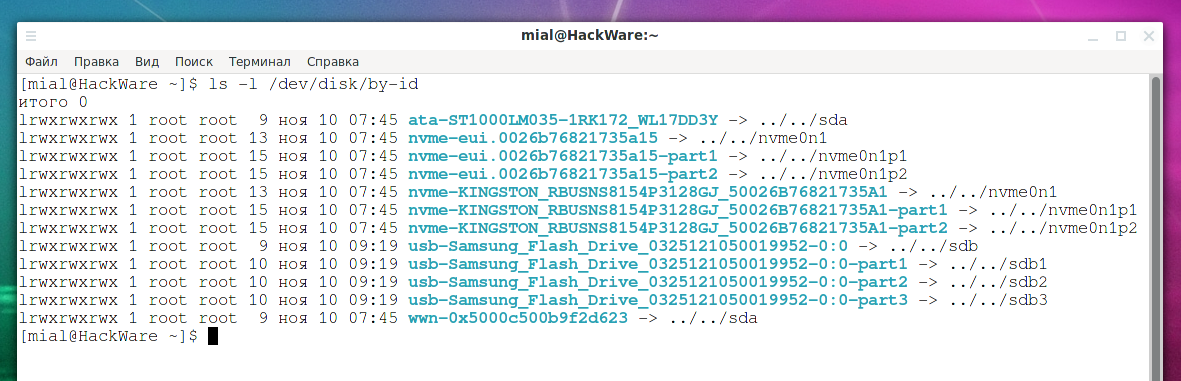
Persistent names for block devices
Posted by Alex On November 10, 2021
Table of contents 1. How to make drives and USB sticks have the same name 2. Persistent block device naming 2.1 by-label 2.2 by-uuid 2.3 by-id 2.4 by-path 2.5 by-partlabel 2.6 by-partuuid 3. Using persistent naming 3.1 Permanent block device names can be used as aliases for /dev/sdX 3.2 Using persistent names in the /etc/fstab filesystem table Conclusion How to make […]

How to change the VeraCrypt interface language in Linux
Posted by Alex On November 7, 2021
Currently, preliminary versions of VeraCrypt have an interface in French, German, Russian and other languages. When localization support is added to the stable version, and this will be done in VeraCrypt 1.25, then to get VeraCrypt with the interface translated into your language, it will be enough to install it as shown above. But currently […]

How to get web page content and cookies of .onion sites in Python
Posted by Alex On November 5, 2021
A program that receives data from the Tor network must work with cookies, for example, in the case of a parser, it can be cURL, PHP script, Python script, and so on. In the article “Web site parsing in command line” there is an example of working with cookies in cURL, but how to get […]

How to repair an LVM disk using fsck
Posted by Alex On November 1, 2021
How to repair an LVM disk If, due to errors on the disk, the system cannot boot, then usually in the emergency mode console you need to check the disk partitions, approximately as follows (you need to specify your disk name and partition number): umount /dev/sda2 fsck -y /dev/sda2 But if we are talking about […]

How to determine why Linux boots into Emergency mode
Posted by Alex On November 1, 2021
How to determine the exact reason why Systemd falls in emergency mode A Linux system can go into an emergency mode shell if it encounters problems during boot. The screen prompts you to execute the command journalctl -xb to find the causes of system problems. It is also proposed to execute systemctl default or exit […]
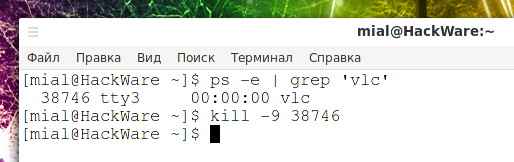
Why doesn’t the kill command kill the process?
Posted by Alex On October 30, 2021
The kill command is used to stop a process, the command syntax is: sudo kill PROCESS-ID Related article: What are the differences and how to use the kill, pkill and killall commands You may run into a situation when using kill does not kill the process. You can get the process ID knowing the name […]