Tag: Information Security

How to enable DNS over HTTPS in Windows 11
Posted by Alex On October 15, 2022
iThemes Security locked out a user – how to login to WordPress admin when user is banned (SOLVED)
Posted by Alex On July 11, 2022

Why computer can’t connect to Wi-Fi Hotspot on Android phone for a long time (SOLVED)
Posted by Alex On June 12, 2022
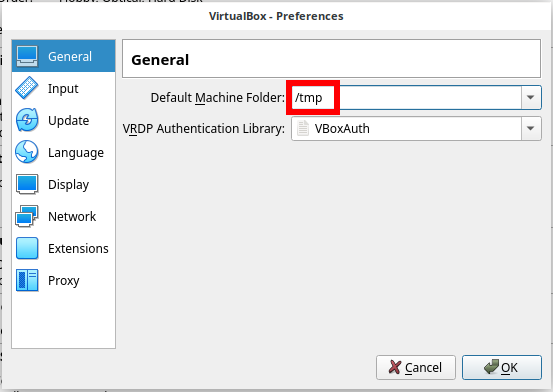
How to make VirtualBox virtual machines destroy on computer restart
Posted by Alex On May 4, 2022

How to change the VeraCrypt interface language in Linux
Posted by Alex On November 7, 2021

How to check IP history for SSH sessions
Posted by Alex On October 15, 2021

Intel disabled undervolting on 11th gen Tiger Lake CPUs
Posted by Alex On May 29, 2021

How to disable autostart of programs and services in Windows
Posted by Alex On May 26, 2021

How to prevent Tor users from viewing or commenting on a WordPress site
Posted by Alex On October 19, 2022