How to use Kali Linux to check web-sites
July 29, 2019
The essence of securing websites comes down to finding problems before a hacker does and fixing it before a hacker exploit it. Hackers are looking for problems with the security of websites (site vulnerabilities) with the help of specialized programs (‘tools’).
Since these programs are “dual-use” - that is, they can be used to ensure the security of sites or to hack sites – they are freely distributed. There are even whole Linux distributions in which these tools are preinstalled. These distributions include: Kali Linux, BlackArch, Parrot Security and others.
Tools for checking sites are freely available, but the problem is that most webmasters do not know how to use them. The situation for them is aggravated by the fact that this is largely a command-line utility, that is, programs without a graphical interface, they need to be run in the console. And it’s still worse that it’s not even a Windows program – most of them are easily installed only in Linux.
I have prepared this very simple tutorial for absolute newbies who have never even seen Linux. With it, you can:
- run Kali Linux in a virtual machine
- check your sites and servers
It will not be difficult, I promise! Let's start.
Download Kali Linux
Go to https://www.kali.org/downloads/, find the Kali Linux 64-Bit option there and download the Torrent file. Then download the system image (I am sure that you are able to use torrents without my instructions).
How to run Kali Linux
Windows users are used to the fact that with the help of the distribution disk image you can only perform the installation. You can also use the Linux image to perform the installation. But it can do another great trick as well – Linux can be run directly from the disk image. That is, the .iso file can be written to a USB flash drive or optical disc and booted from it into Linux and working there as in a full system. This is called a live system.
The advantages of this method:
- instant start, no installation required
- can be run from a flash drive – safe for your primary operating system
There are disadvantages:
- all changes made to the operating system disappear after a reboot.
As I promised that it will be easy, we will choose the work in the Live-system. If you have further interest, then you can install Linux in a virtual machine or as a second operating system.
Running Kali Linux without installation
The downloaded image can be recorded on a USB flash drive using Etcher (there are only three buttons in this program – you will not get confused) and boot from this flash drive.
But there is an even simpler option! Run a live Linux system in a VirtualBox virtual machine.
So, since we will run Kali Linux in VirtualBox, in this case we DO NOT need to burn an ISO image to a USB flash drive, we just need to install VirtualBox, this is done elementary.
Creating a virtual machine for Kali Linux
We all know that the computer has one operating system. We can install a second operating system (for example, a different version of Windows or a Linux distribution), but in order to switch to this other operating system, you need to shut down the computer and select another OS when booting. So, the VirtualBox program removes this restriction – it allows you to run two or more operating systems on one computer simultaneously, each of which works independently of the other!
This is achieved through the “virtual computers” (“virtual machines”) for which VirtualBox is responsible.
So, let's create our virtual machine, in which we will run Kali Linux.
1. Open VirtualBox
2. Click the Create button:
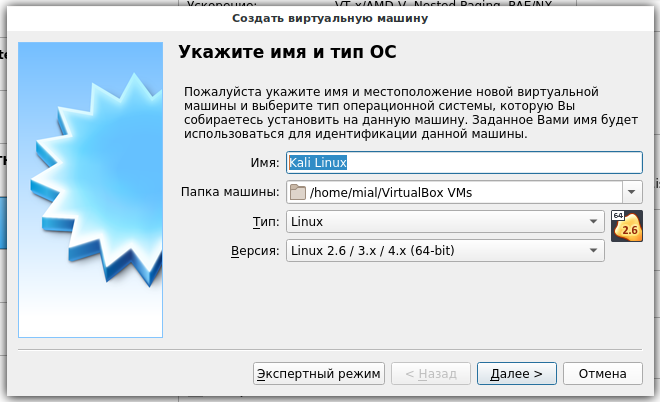
3. Enter the Name ‘Kali Linux’, click Next.
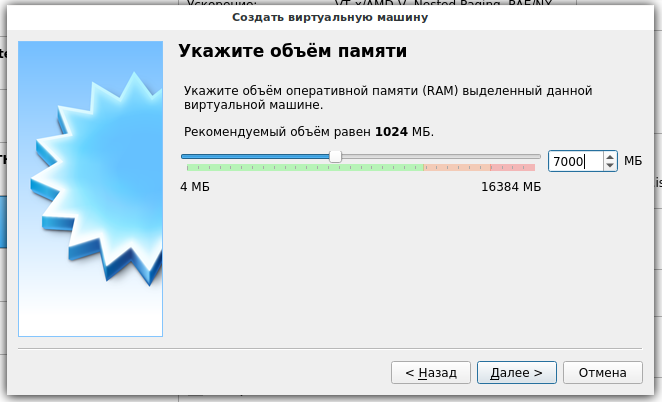
4. Set the amount of RAM you allocate to the virtual machine – 4 gigabytes or more is recommended. But remember that the allocated memory is taken from your main OS, that is, leave enough of it so that your main OS also works properly. Press ‘Next’.
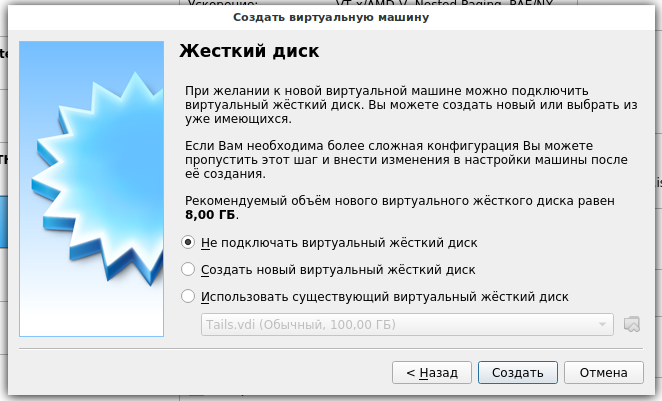
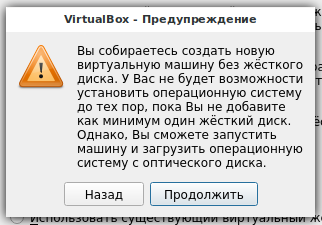
5. We do not need a hard disk, since we will work exclusively in the Live-system. Therefore, select ‘Do not attach a virtual hard disk’. And click the Create button.
6. The system thinks that we do not know what we are doing, but we know! Therefore, click the Continue button.
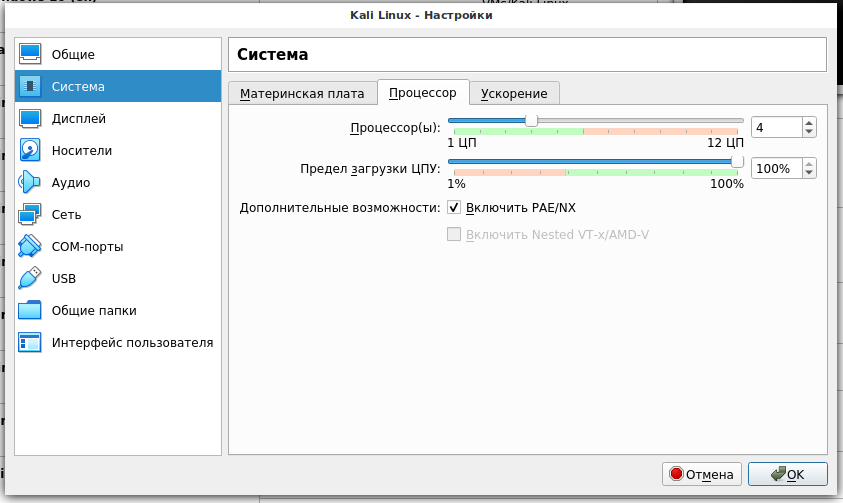
7. This step is optional. Go to the virtual machine settings (select it and click the ‘Configure’ button, or right-click on the virtual machine and select ‘Configure’ in the context menu). There, in the System section on the CPU tab, I recommend adding the number of cores (to make it work faster) and tick the “Enable PAE/NX” box. When changes are made, click the OK button to save them.
Running Kali Linux for a newbie
Now start the virtual machine – double click on it or click the Run button.
A black screen will appear (at this stage, this is normal):
In the menu, go to Devices → Optical Discs → Select Disk Image:
Select the Kali Linux image that you recently downloaded.
Before rebooting, we will make another setting. In the menu, go to Devices → Shared Clipboard → Bidirectional.
And now in the menu select Machine → Reboot.
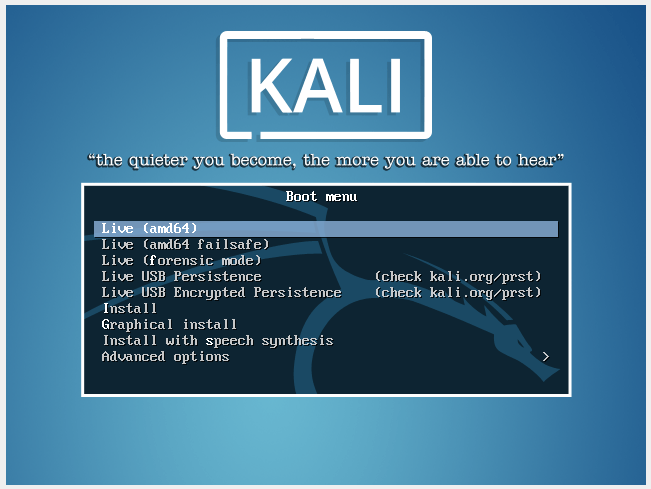
And here is the famous Kali Linux:
Press ENTER to boot.
Kali Linux console
Now we will work on the command line (Linux console). To open it, click on this icon:
Top Kali Linux Commands for Newbies
Checking WordPress sites in Kali Linux
WPScan is used to check WordPress sites. This program can identify old versions of WordPress, the WordPress theme, installed plugins, show known vulnerabilities in plugins and themes of WordPress.
Let's start with updating the database (you need to do it once after booting the computer):
wpscan --update
To check the sites run the command:
wpscan --url SITE.COM -e p,vt,u
For example, if I want to check the site www.forum.comp-web-pro.ru, then the command is as follows:
wpscan --url www.forum.comp-web-pro.ru -e p,vt,u
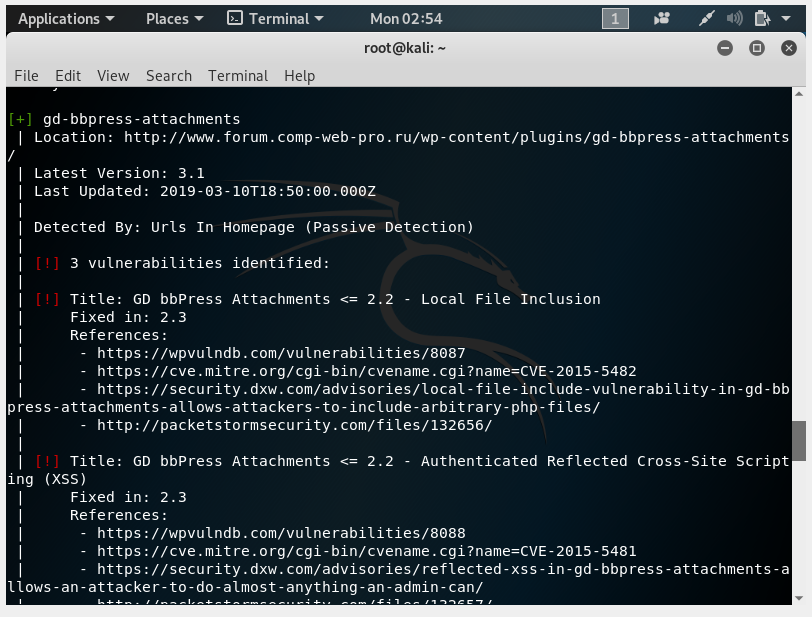
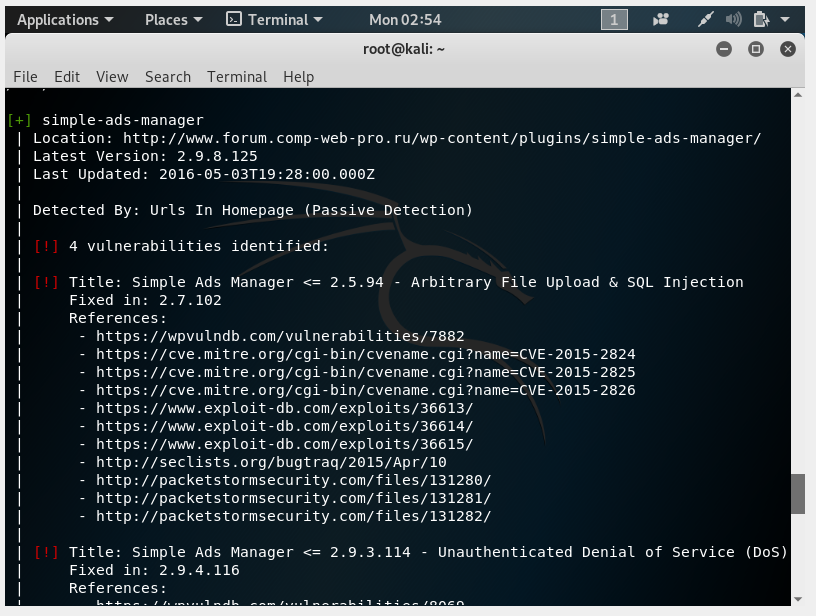
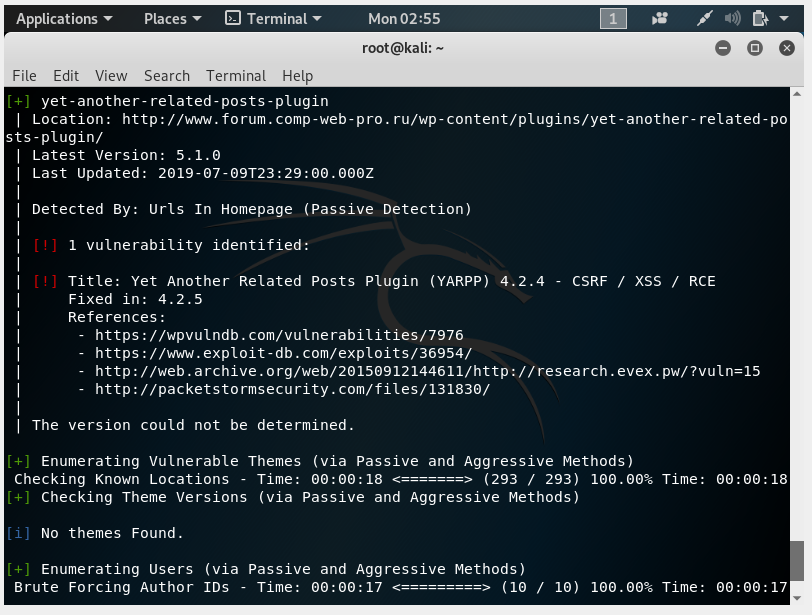
It is determined that registration is available on the site, WordPress version is found, the theme is defined.
Found many vulnerabilities in installed WordPress plugins:
How to run Nikto Scan
Nikto is a web server security auditing tool. It is designed to search for various default and insecure files, configurations and programs on web servers of any type.
To scan with Nikto, you need to run a command like this:
nikto -h https://DOMAIN.COM
Please note that the protocol also needs to be specified.
An example of launching a scan of the site https://www.forum.comp-web-pro.ru/:
nikto -h https://www.forum.comp-web-pro.ru/
The information displayed may be about serious errors, as well as less important shortcomings (for example, the HTTP protocol security headers are missed).
Finding SQL Injection Vulnerability
The sqlmap program is useful to those webmasters who program and write the code of services, CMS, web sites. Using sqlmap, you can find SQL injection vulnerability.
SQL injection is one of the most serious vulnerabilities in web applications. When starting the program, you need to specify the parameter being tested, example:
sqlmap -u https://DOMAIN.COM/rubrika.php?id=31
How to find out web technologies of a website
You can check that the hacker can find out about the technologies used by your site. Or you can see for yourself the technologies of another site. This is done by WhatWeb.
To do this, use the command:
whatweb SITE.COM
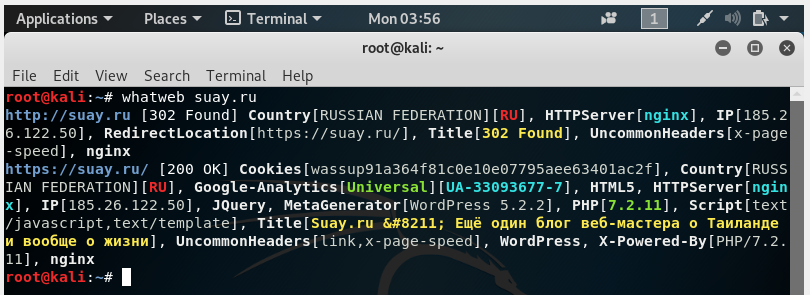
For example, I want to get information about the suay.ru site:
whatweb suay.ru
Web application information gathering
Wig is a web application information gathering tool that identifies a number of content management systems (CMS) and other administrative applications.
Install the program:
apt install wig
To check a site, run the following command:
wig https://DOMAIN.COM
Check that you can find about the suay.ru site:
wig https://suay.ru
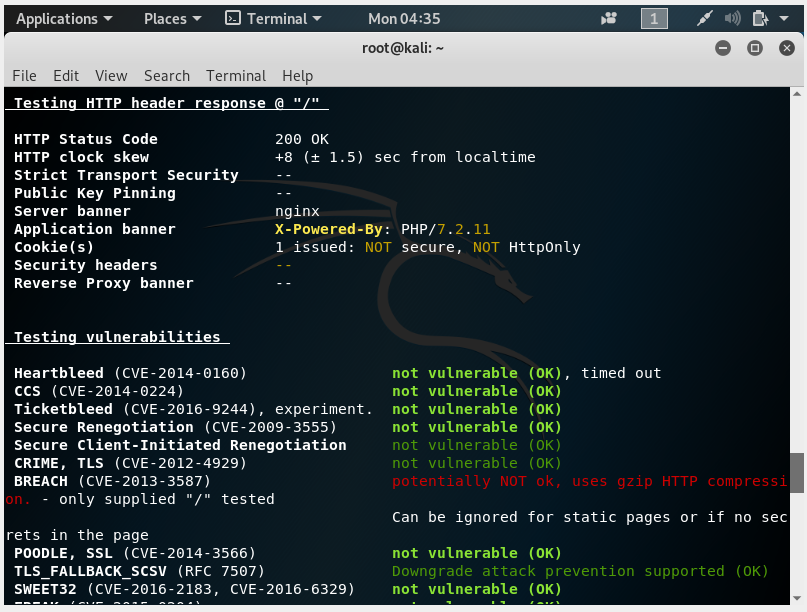
Verifying the SSL certificate configuration
With the help of the testssl.sh program you can check whether everything is all right with your SSL certificate, whether it is installed correctly, whether the SSL setting contains probabilities of using vulnerable ciphers, etc.
Install the program:
sudo apt install testssl.sh
To check, run the command:
testssl SITE.COM
Check the correctness of TLS/SSL settings of the suay.ru site:
testssl suy.ru
How to find open ports
Checking open ports can be done with the Nmap program.
There is nothing bad to have open ports while the services behind them are safe. For example, open ports 443 and 80 are required for the web server to work. That is, ports must be open for the services that are used currently.
Ports should be closed for unused services. For example, if you do not need an FTP server, then port 21 should not be opened, if you are not using SSH, then port 22 should not be open.
If you find an open port with an unusual number, this may mean that the server was hacked and the hacker installed a backdoor on this port.
First of all, you should check your own servers (VPS), since virtual hosting usually have many ports open and the hosting provider does it for some of their needs.
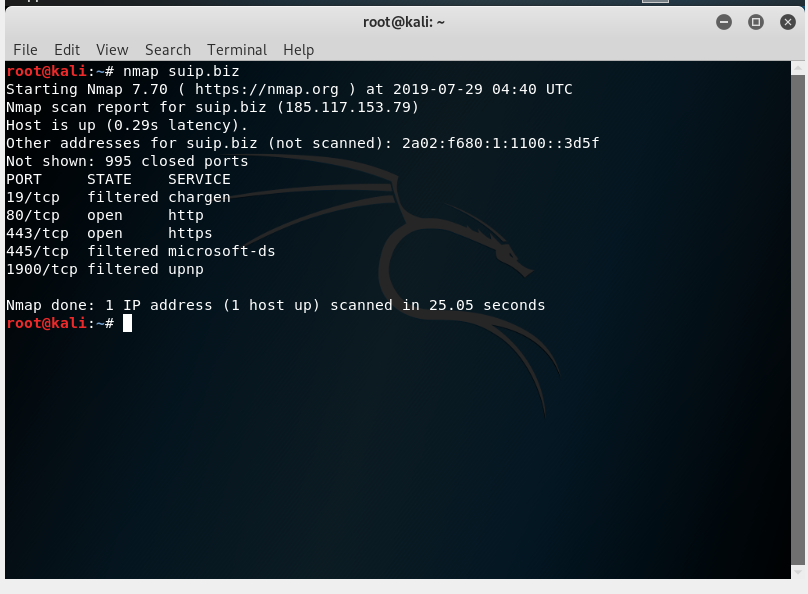
To check open ports, use the Nmap command.
The command runs as follows:
nmap IP_or_SITE
In this case, the most frequently used ports will be checked. If you want to check all the ports at all, then run the command like this:
nmap IP_or_SITE -p-
Check the open ports of the server running the suip.biz website:
nmap suip.biz
How to find out if a domain is available for registration
Suppose you want to know if a domain name is busy, but you do not want to trust third-party services and sites. You can do the check right on your computer!
This can be done, for example, using the whois command. Run it as follows:
whois SITE.COM
Suppose I want to know if the domain w-e-b.site is busy:
whois w-e-b.site
If the domain is already registered by someone, the corresponding registration information will be displayed. If the domain is not used by anyone, it will be deduced that the domain was not found (data was not found, no records were found, etc.). Examples of records if the domain does not exist:
- No entries found
- No Data Found
- The queried object does not exist: DOMAIN NOT FOUND
- etc.
How to view HTTP headers
The HTTP headers may contain information about redirection, the server and so on. You can view the HTTP headers with the following command:
curl -I SITE.RU
Viewing HTTP headers when accessing suay.ru website:
curl -I suay.ru
Example output:
HTTP/1.1 302 Moved Temporarily Server: nginx Content-Type: text/html; charset=iso-8859-1 Connection: keep-alive Location: https://suay.ru/ Date: Mon, 29 Jul 2019 06:48:23 GMT X-Page-Speed: 1.13.35.2-0 Cache-Control: max-age=0, no-cache
A redirect is being performed, the Location: https://suay.ru/ line says this.
How to find the IP address of the site
There is nothing easier than finding the IP address of any site. To do this, run the command:
dig SITE.COM +short
For example, I want to know the IP address of the site suay.ru:
dig suay.ru +short
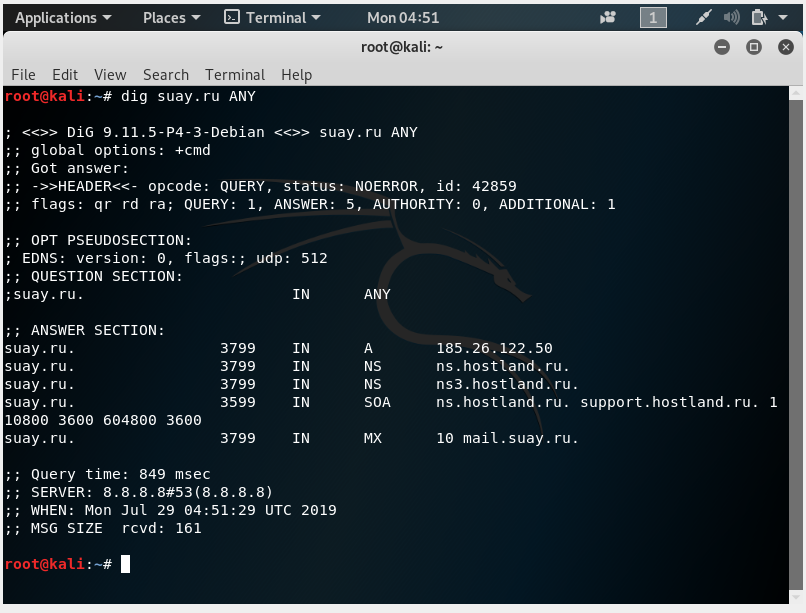
How to find out all the DNS records of the site
All DNS site records can be obtained with a command like:
dig SITE.RU ANY
Example for the suay.ru site:
dig suay.ru ANY
Kali Linux for absolute newbies
Perhaps it is enough for the first start.
In fact, I could continue for a long time: how to search for hidden files and folders on the site, how to find out subdomains, how to check for other vulnerabilities, how to find all sites on one IP address and so on – and this is just about sites! Many interesting things can be told about other topics with Kali Linux: about Wi-Fi, for example. Therefore, if you have an interest in this topic, then I will continue. You can show your interest by sharing a link to this article on a social network or on your website. There will be visitors to this article – there will be a sequel.
Related articles:
- How to block by Referer, User Agent, URL, query string, IP and their combinations in mod_rewrite (75.9%)
- How to protect my website from bots (75.9%)
- How to reboot a server in DigitalOcean (67.6%)
- How to run small Python code in Bash (50%)
- How to completely uninstall a package along with dependencies on Arch Linux (as well as BlackArch and Manjaro) (50%)
- How to show all errors in PHP 8 (RANDOM - 50%)